What’s The Best Algorithm For User Credential Storage In 2024?
User credential (which refers to username and password combinations used for accessing online accounts) are very sensitive data sets that must necessarily be protected. Attack to such data sets lead to the financial ruin, sabotage or exposure of confidential materials belonging to individuals and financial and integrity ruin for organizations.
There has been appreciable development in the evolution of storage algorithms. Some existing storage algorithms include, the MD, SHA, Bcrypt, Scrypt and Argon. Presently, Argon2 seems the holy grail of storage algorithms when it comes to user credentials. This is due to its remarkable flexibility and superior security capabilities.
In what follows, I will analyze why Argon2 take the number one spot on my preference list and why other alternatives trail behind rather sluggishly.
Your essential Linux handbook
Want to level up your Linux skills? Here is the perfect solution to become efficient on Linux. 20% off today!
Download now
User Credential Storage Algorithms to Avoid
MD5
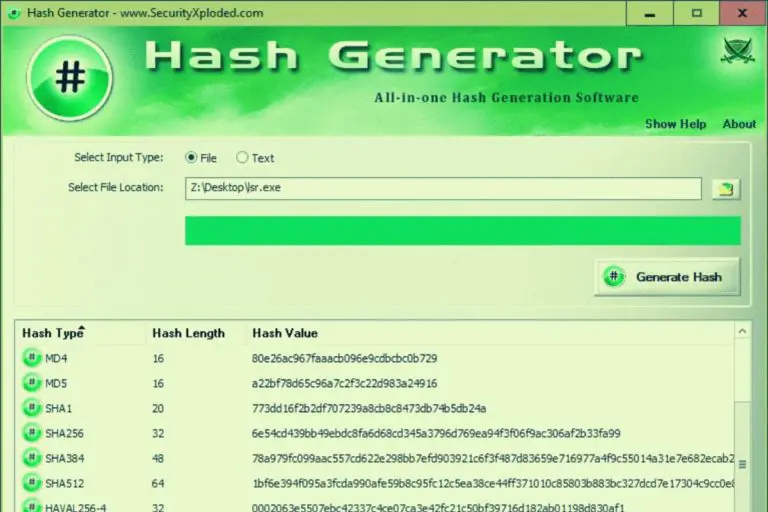
One of the oldest credential storage algorithm is the Message Digest Algorithm (MD5). The MD5 is a cryptography hashing algorithm. It constitutes part of the larger Message Digest Algorithm cluster which originally was created to authenticate the integrity of hashed message. MD5 is the product of incremental developments made on the earlier installments of the Message Digest Algorithm which are the MD2 and MD4.
Try it for free now, with advanced security features.
2900+ servers in 65 countries. It's free. Forever.
MD5 is used for a variety of reasons including the storage of employee credentials. However, the MD5 has been appraised by numerous expert bodies and due to the results of numerous security analysis to be insecure and therefore not to be used on any applications.
In addition, the MD5 is a memory saving algorithm and this design allows the hacker to figure the hash of very huge number of passwords in a short time using the ASICs or FGPA arrays.
A major problem of the MD5 is that the MD5 password hashes are very fast. This means that hackers can find their way into the system by trying many password possibilities. This implies that with the MD5, brute force attacks are more likely than not to occur.
Download your exclusive free PDF containing the most useful Linux commands to elevate your skills!
Experts therefore recommend the Secure Hash Algorithm (SHA) in place of the MD5 to combat its weaknesses.
SHA
The Secure Hash Algorithm (SHA) are a cluster of cryptographic hash functions. It was originally designed to improve on the weaknesses of the MD4 which was the second development of the Message Digest Algorithm family. It breaks credentials into smaller bits and creates a string of 160 bits (20 byte) also known as message digest.
The cryptographic functions are used to store data in the form of three different characteristics, such as pre-image resistance and collision resistance.
- Elimination of the Weaknesses of MD5: By collision resistance, the SH algorithm eliminates the weakness of the MD5 system which makes it possible for new words with the same hash to be sent into the system. With this, it prevents the validation of malicious contents and files and by pre-image resistance, SHA eliminates the possibility that two passwords in the system will have the same hash identity.
- Time Consuming for Hackers: It makes it more time consuming for hackers to break into any system. There are four SHA algorithms which are SHA 0, SHA 1, SHA 2, and SHA 3, each possessing minor modifications and advancements on the weaknesses of the other.
Weaknesses of the MD5 and SHA Algorithms:
The MD5 and SHA clusters are extremely fast when it comes to data computation but this is not necessarily good for password storage for the following reasons:
- Faster computing makes it easier for brute-force attacks to prevail. Hence, making organizations vulnerable to such attacks.
- In addition, MD5 and SHA don’t have mandatory salt as added protection for the storage of hashed passwords.
While MD5 and SHA algorithms clusters are not without their numerous advantages, experts have advised against using them due to their vulnerability to the increasingly sophisticated dynamics of cyber-attacks within the business environment to gain access to employee credentials.
Top 3 algorithms to choose for storing user passwords
Bcrypt
Bcrypt, unlike MD5 and SHA includes additional protection which makes it impossible for brute force attacks to prevail. Bcrypt is often referred to as CPU hardened algorithm. Meaning that computing a single hash on the Bcrypt system requires multiple CPU cycles.
Unlike MD5 and SHA, Bcrypt increases difficulty and impenetrability to brute force system entry. Bcrypt allows one to design a number of iterations using specific work factors which slows down computing speed. One can simply increase work factor of the Bcrypt to increase resource consumption. This also makes it a mandatory requirement for hackers to deploy very expensive campaigns and huge time efforts to breaking through Bcrypt systems. Thus making brute force entrance almost impossible when the bcrypt algorithm is utilized.
Bcrypt, however, provides very limited security and its weaknesses to a large extent are protected by another storage algorithm known as Scrypt.
Scrypt
Scrypt is also a hardened function but is very advantageous because it consumes a lot of memory space. Script provides ample room for control and flexibility as the developer employing the algorithm can determine the memory and computing resources required.
Download your exclusive free PDF containing the most useful Linux commands to elevate your skills!
In other words, attack campaigns against Scrypt algorithms are very cost intensive due to their huge memory and computation requirements.
When it comes to memory hardness, Scrypt is preferable to Bcrypt and has a wide usage with implementation of the ASIC and FGPA technologies on it. At best, however, Scrypt no doubt provides an improvement on the weaknesses of Bcrypt, yet, the protection it provides is far from perfect. The loopholes of Bcrypt and Scrypt led to the development of the Argon storage algorithms.
Argon 2
The Argon 2 algorithm provides the most flexibility. It won the password hashing competition in July 2015. It is considered an improvement on the Bcrypt and Scrypt algorithms, it has a pre-defined memory size, the element of CPU time and parallelism.
Join the Complete Ethical Hacking Course Bundle and step into the world of cybersecurity.
Learn to think like a hacker and protect systems with this comprehensive course.
These elements combine to make brute force attacks very expensive because it requires attackers to have large memories for computation and memory resources. Argon2 has the 2i and 2d variations. The former is effective in protection against side channel attacks while the latter provides stronger protection against GPU cracking attacks.
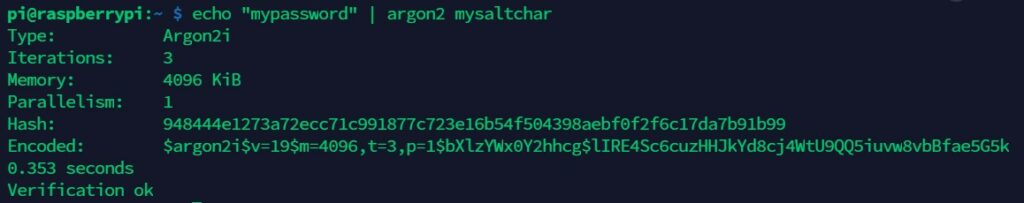
Argon2i employs an isolated memory access, which is best for password storage. The hybrid version of the Argon storage technology complements combines the strength of 2i and 2d to provide all rounded security. Argon2id performs as 2i for at least 50 percent of the first iteration over the memory and as 2d for the rest of the operations.
The storage technology, unlike Bcrypt and Scrypt, provides protection against side-channel attacks and brute force entries as well as tradeoff attacks
Argon2 converts password inputs from their human readable form to a string of gibberish which cannot be converted back to original inputs from which they were created. And when database is lost while the created string of gibberish is lost, the original value remains intact.
Argon2’s fundamental design makes it resistant to tradeoff attacks and makes it more difficult to cheaply optimize on-field programming gateway arrays. Argon2d employs memory access which depends on data, making it suitable for cryptocurrencies and other applications to heave sighs of relief when it comes to side channel timing attacks.
It is quite clear, more so, proven by security investigations, that the Argon storage algorithms provides the best protection when compared to earlier listed algorithms. I therefore present to you, without a shadow of doubt the most reliable user password storage algorithm, its name, Argon.
Whenever you’re ready for more security, here are things you should think about:
- Break free from Gmail:
You should be able to choose what happens to your data. With Proton, only you can read your emails.
Get private email.
- Protect yourself online:
Use a high-speed Swiss VPN that safeguards your privacy. Open-source, no activity logs.
Get Proton VPN risk-free.
- Master Linux commands:
A sure method to learn (and remember) Linux commands. Useful ones only, one at a time, with clear explanations.
Download the e-book.