Can Hashed Passwords Be Decrypted? (Not as safe as you think)
Most of the time, the passwords you use on your favorites websites are not stored in plain text. They are first hashed for security reasons. But if someone gets access to the database with all logins and passwords, can the passwords be decrypted? That’s what’s we’ll talk about in this article.
As a general rule, passwords are stored by using a non-reversible hashing algorithm, so they can’t be decrypted directly. Some solutions exist to try to recover the plain text version of a hashed password, but it’s generally time-consuming and without any guarantee.
I’ll explain everything in details in the following (passwords storage, hashing algorithm and reversibility), feel free to skip some sections if you already know them pretty well.
Your essential Linux handbook
Want to level up your Linux skills? Here is the perfect solution to become efficient on Linux. 20% off today!
Download now
How Are Passwords Stored?
Try it for free now, with advanced security features.
2900+ servers in 65 countries. It's free. Forever.
Developers will first convert the plain text password into an encrypted version of it, by using a hashing function of their choice. Then, they’ll store the hashed version in a database, associated with your login or email address.
Hashing functions will turn your plain text password (“lovemom123”) into a new sequence of character that may seem random at first sight (something like “127c9a696ed93cd06cca726a862c3127”). This way, developers will never see your real password, and if the database or storage is hacked, it will be safer as the hacker won’t get direct access to all emails and passwords directly.
It’s not perfect, as we’ll see later in this article, but it’s a pretty good process to avoid most issues.
Download your exclusive free PDF containing the most useful Linux commands to elevate your skills!
I have a complete article on this topic if you are interested, so I won’t be longer here: How Are Passwords Stored? (5 Methods Used by Developers)
How Do Hashing Algorithms Works?
A hashing algorithm is a cryptographic function that convert any input of data to a fixed-size representation of this input data, what is named the hash.
Theory
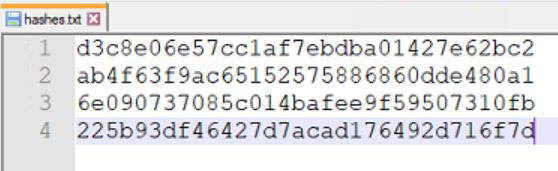
As an example, one of the most popular hashing algorithm is MD5. It will turn any input file or string to a 32 hexadecimal characters string (more details here). It means that whatever the length of your password, or the size of your ZIP archive, it can generate a 32 characters string from it.
Obviously, as the size of the output data is limited to 32 characters, collisions exist. It means that two different input files (or string to a lesser extent) can produce the same hash result (read my article about this):
But the probability to have this kind of issue is so low that it doesn’t really matter, especially for passwords that are generally shorted than the output string.
Try it yourself!
If you are new to this and want to play with it a bit, heads to MD5Online and try to create hashes with a few words. It’s fun, and it’s the best way to remember this.
Each time you enter a different word in the form, you’ll get a new hash, the corresponding MD5 value of the word you typed. MD5 is less and less used to save passwords, but it’s the same idea for any algorithm.
Back to your main question now, is it safe enough?
Can Hashed Passwords Be Decrypted?
Download your exclusive free PDF containing the most useful Linux commands to elevate your skills!
Hashed passwords can’t be decrypted. The hashing functions are not reversible, so there is no way to directly get back a password from its hashed representation. However, some algorithms are less secure than other, and strategies like brute-force or rainbow tables may still work to recover some passwords.
I also need to explain something important: hashing and encryption are not the same thing.
- Encryption: it’s a two-way function, so anything that is encrypted can be decrypted by using the same key.
Ex: OpenSSL, Drive Encryption, etc. - Hashing: it’s a one-way function, there is basically no-way to recover the original password.
Ex: MD5, SHA-1, etc.
As passwords are stored using a hashing algorithm, they can be decrypted, they are not “encrypted”.
Secure your spot in the Accelerator Program, with early access to exclusive resources.
Get 1000+ classes, unlimited mentorship, and more.
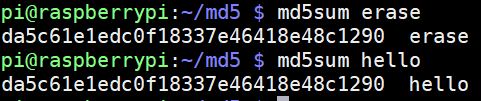
The warning I mention here, is that some algorithms are no longer safe enough to be used to store passwords. For example, there are databases of billion of passwords existing for the MD5 algorithm, so it’ll be easy to recover a password stored in MD5 without salt (here is a free decryption tool for MD5 as an example).
It’s the same thing with most “fast” algorithms. Current computers can generate countless hashes in one second, so any algorithm that is not time-consuming for the computer (CPU or graphic card), it’s generally not the safest. If your home computer can generate millions (or billions) hashs per second, imagine what a super computer can do.
I explain different strategies on this page, and in more details in my book that you can find here.
That’s how we get that kind of result, leading to the recommendation to use at least 15 characters passwords:

More details here: Is MD5 Easy to Crack? (and how long does it really takes)
Whenever you’re ready for more security, here are things you should think about:
- Break free from Gmail:
You should be able to choose what happens to your data. With Proton, only you can read your emails.
Get private email.
- Protect yourself online:
Use a high-speed Swiss VPN that safeguards your privacy. Open-source, no activity logs.
Get Proton VPN risk-free.
- Master Linux commands:
A sure method to learn (and remember) Linux commands. Useful ones only, one at a time, with clear explanations.
Download the e-book.