How to Get an MD5 Hash in PowerShell?
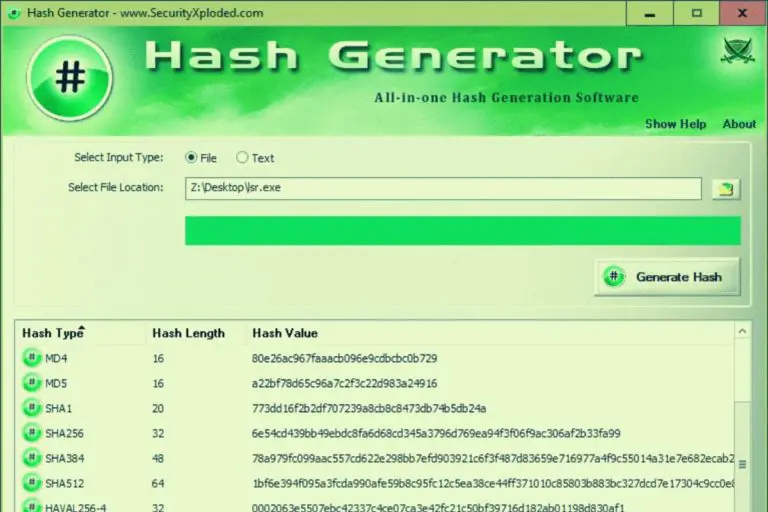
MD5 is a hashing algorithm, still popular despite the security issues. You can use it to encrypt a string or to get the fingerprint of a file. In this article, we’ll see how to use it in PowerShell. PowerShell offers a cmdlet to generate MD5 hash for a file: Get-FileHash. It can also be used…