How to Know if a Hash is a MD5? (Vs SHA1 and SHA256)
That’s a common question when you work with hashes for the first time. I’m not (yet) native speaker in MD5, but I think I can help you to guess if a hash you have is a MD5 or not.
The MD5 algorithm generate 128-bits long hashes, generally represented in a string of 32 hexadecimal characters. SHA-1 is 40 characters while SHA-256 is 64 characters.
So, that’s pretty easy to guess which hash type you have just with this short answer. But keep reading if you want to learn more and discover the tools you can use to help you.
Your essential Linux handbook
Want to level up your Linux skills? Here is the perfect solution to become efficient on Linux. 20% off today!
Download now
What does a MD5 hash look like?
Join the Complete Ethical Hacking Course Bundle and step into the world of cybersecurity.
Learn to think like a hacker and protect systems with this comprehensive course.
A MD5 hash is a 128 bits message digest represented as 32 hexadecimal characters (0-9 and A-F). For example, “700527793dc07905fd9778bad5665e44” is a MD5 hash.
The hexadecimal system is a representation of the base 16, so 16 symbols: 0123456789ABCDEF.
Most hashes are represented using this system, and MD5 use 32 hexadecimal characters for this.
The case doesn’t matter by the way.
- 9bdf52a483077 is not a MD5 hash because it doesn’t have 32 characters
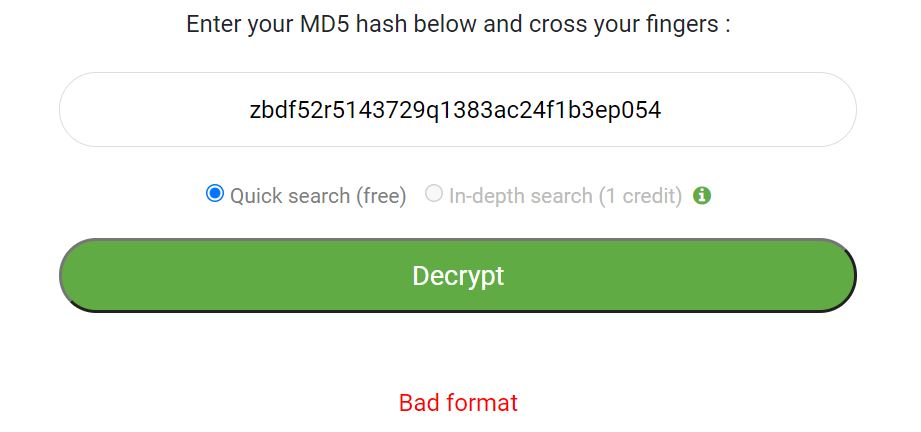
- zbdf52r5143729q1383ac24f1b3ep054 is not a MD5 hash because it’s not hexadecimal
- 84e5f5b9dad87e723b37de2e5c4cf072 has the correct format to be a valid MD5 hash
Download your exclusive free PDF containing the most useful Linux commands to elevate your skills!
If you put your hash in our MD5 decryption tool, it will tell you directly if it’s not a MD5 hash. Here is an example with the second one:
If you are interested, I have an entire article where you can see a few regular expressions to match MD5 hashes.
Differences with other hash functions
Other popular hashing algorithms have similar format, but they also have a big difference that should help you to quickly find which type of algorithm has been used to generate the hash.
What does a SHA1 hash look like?
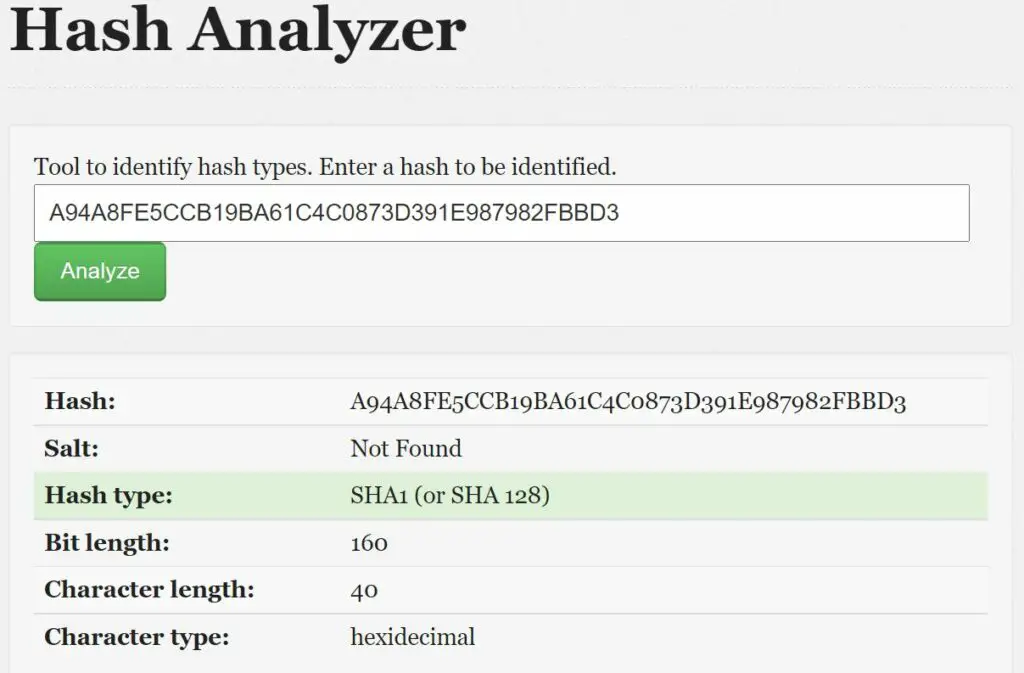
The SHA1 algorithm generates a 160-bits message digest, represented as a 40 characters hexadecimal number. For example, “A94A8FE5CCB19BA61C4C0873D391E987982FBBD3” is a SHA1 hash.
So, the easiest way to check if your hash is SHA1 or MD5 is to count the number of characters. You can use a letters counter tool like this one to do this. If it’s 40 characters, it’s a SHA1 hash, 30 characters it’s MD5, anything else is none of them.
The regular expression corresponding to a SHA1 hash will be something like “/^[A-F0-9]{40}/i”.
I also have an article about the difference between SHA1 and MD5 if you are interested.
What does a SHA256 hash look like?
Download your exclusive free PDF containing the most useful Linux commands to elevate your skills!
As a general rule, a SHA256 hash is represented as a string of 64 hexadecimal characters. Hexadecimal characters can be 0 to 9 and A to F only.
So again, if you hash is 64 characters long (by using the tool linked above) and is only hexadecimal character, there is a big chance it’s a SHA256 hash.
The regular expression corresponding to a SHA256 hash will be something like “/^[A-F0-9]{64}/i”.
By the way, you can learn about the difference between MD5 and SHA256 here.
Secure your spot in the Accelerator Program, with early access to exclusive resources.
Get 1000+ classes, unlimited mentorship, and more.
Tools to identify a Hash Type
Hash Analyzer is one of the best tools to identify a hash type. By giving a hash input to this tool, it gives an instant result of which type of hashing algorithm has been used to generate your hash (MD5, SHA1, SHA256 and many other).
You can use this tool for free here.
But now that you know the main differences between MD5, SHA1 and SHA256 hash, any letters counter tool will be enough for you 🙂
I hope this article was useful for you, and remember that if you are a bit lost with all these hashing functions, I have many articles on this topic, for example:
- How to Convert MD5 Passwords to SHA256?
- Is MD5 Reversible? (Truth, Myths and Solutions)
- How to Open an MD5 File on Any System?
Whenever you’re ready for more security, here are things you should think about:
- Break free from Gmail:
You should be able to choose what happens to your data. With Proton, only you can read your emails.
Get private email.
- Protect yourself online:
Use a high-speed Swiss VPN that safeguards your privacy. Open-source, no activity logs.
Get Proton VPN risk-free.
- Master Linux commands:
A sure method to learn (and remember) Linux commands. Useful ones only, one at a time, with clear explanations.
Download the e-book.